Firewall Logs on Azure VMs
Friday, October 12, 2012
by asalvo
The more configuration you can manage via Group Policy, the easier your life is going to be. Today, I was reviewing the configuration I had in place for firewall logging for my Azure VMs. I realized that I had reached a point where I needed to firm up my standards, and using Group Policy was a great way to do that. I came across one snag which I felt would be worth mentioning and decided to go over my entire setup.
Log File Location
If you use any of the standard windows images provided by Microsoft, you end up with a 30GB system drive. With Windows Server 2012, that leaves you anywhere between 15 and 20GB of free space. For this reason, I like to install everything to a secondary drive, as well as configuring logging to use a secondary drive.
My first drive that I created for my Azure VM’s, ends up being F. This is where I install all my program files to, and configure logging. Using group policy you can define a well known folder structure, which will make it easier to automate log archiving and pruning. My folder structure around logging is:
- F:\
- DevOps
- Logging
- Application
- Firewall
- FTP
- IIS
DevOps contains other folders which are used to manage the server and my environment on Azure as a whole.
In order to configure you folder structure using group policy, start by opening up the group policy which you will use. I am using my default domain policy, and do not feel the creation of extra logging folders such as IIS and FTP on machines which do not have IIS or FTP is worth the effort of creating more fine grained policies.
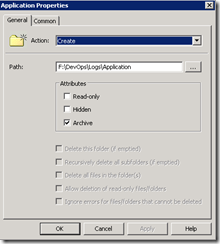
First you need to define your folders, which is done under Computer Configuration\Preferences\Windows Settings\Folders. Right click on Folders, and select New\Folder. Then browse to the folder you wish to add. I chose the Create action, and left all the rest of the defaults.
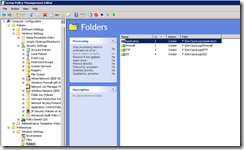
When finished, you should have something that looks like this.
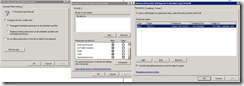
Next, we have to adjust the security settings for our Firewall logs folder. Failure to do this will result in no logs being created. File System security is located under Computer Configuration\Policies\Windows Settings\Security Settings\File System. Right click on File System and choose Add. This operation requires that the folder you want to work with exist on the computer that you are editing the group policy on.
After selecting your folder, you then have to set the security. Remove all of the existing users and groups, and add “NT Service\MpsSvc” and give the user Write Permissions. Then click on Advanced and check the box to “Include inheritable permissions from this object’s parent”. On the security policy dialog, leave the option as “Configure this file or folder then Propagate inheritable permissions to all subfolders and files”.
What this will do, is take your existing security from your DevOps\Logs folder and apply it to Firewall, as well as add NT Server\MpsSvc.
Firewall Settings
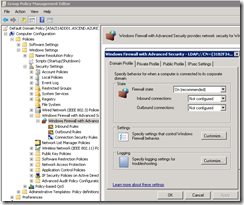
To change the logging (and other settings for the firewall), you need to go to Computer Configuration\Policies\Windows Settings\Windows Firewall with Advanced Security and right click on Windows File with Advanced Security (not the folder, but the child) and choose properties. From here you can turn the firewall on or off for each profile, and configure logging which is what we are interested in.
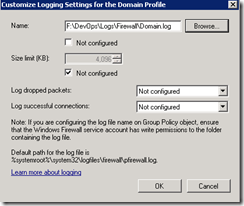
Click on Customize in the logging section to bring up the configuration dialog. You will want to uncheck the box that says Not Configured under the Name and select your path, including the file name. For me this is F:\DevOps\Logging\Firewall\Domain.log.
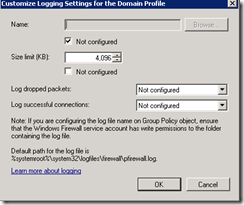
Then click OK to close out of the dialogs. Here is an interesting note, when I go back to the logging configuration dialog, my path is blank and the box for not configured is checked. However, my settings are still applied on the client machines.
Summary
In this post I have shown you how to configure a well known folder structure for logging using Group Policy. Also by using Group Policy we can specify the location of our firewall log files. This is important on Azure VM’s as you do not want to use up your limited space on your System drive when using the default Microsoft Images.